Beautiful Work Info About What Is A Source String

Unraveling the Mystery
1. Source Strings
Ever stumbled upon a chunk of seemingly random characters and wondered what on earth it meant? Chances are, you might have encountered a source string! Its one of those tech terms that sounds intimidating but is actually quite straightforward once you break it down. Think of it as a behind-the-scenes label, a secret ingredient that helps computers (and sometimes, even us humans) understand where something came from or what its all about. It's the breadcrumb trail of the digital world! Forget about any complicated jargon for now; we'll take things easy.
At its heart, a source string is a sequence of characters used to identify the origin or nature of data. This data can be anything from a simple text message to a complex piece of software. It's a bit like the return address on an envelope, or maybe the tiny "Made in..." label on your favorite gadget. It tells you where the information originated, what processes it might have gone through, and, depending on the context, can provide valuable clues about its purpose. This tiny label provides important information.
Now, why is this important? Well, imagine you're a detective trying to solve a digital mystery. You find a file, but you have no idea where it came from. A source string, if present, could be the key to unlocking the entire case! It could point you to the application that created the file, the server it was downloaded from, or even the individual who last modified it. This is where the real power of source strings comes into play. Without them, data lineage becomes a murky and confusing mess.
Think of it like this: when you read a news article, you expect to see a source, whether it's a news agency, a journalist's byline, or a quoted expert. The source gives the information credibility and context. Source strings do the same for digital information. They provide a traceable path and validate, hopefully, the data you're working with. It's all about trust, and in the digital world, trust is something you earn, not assume. This whole string situation becomes pretty important, doesn't it?

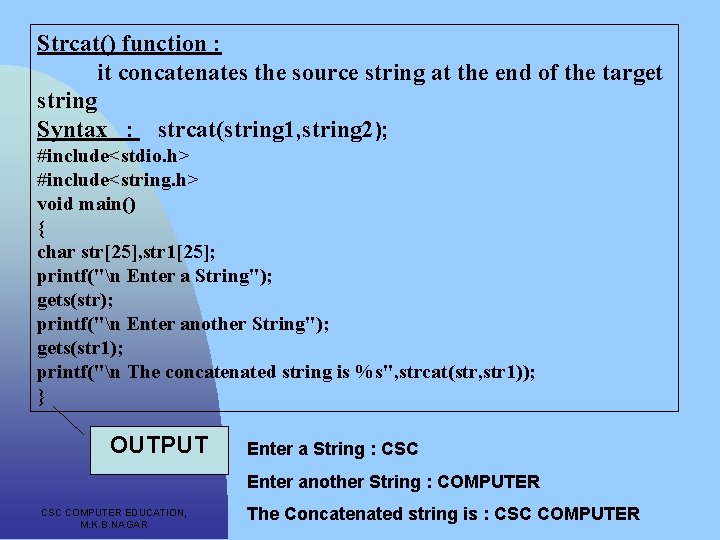
Windows Which Encoding Are My Source Strings In? YouTube
Deciphering the Code
2. Source Strings in Everyday Tech
Okay, enough with the abstract talk. Let's get down to some real-world examples. Youre probably interacting with source strings more often than you realize. Ever notice those long, complicated URLs when you share a link on social media? Those often contain source strings that tell the platform where the link was shared from. This information is precious for tracking user behavior and measuring campaign effectiveness. Imagine trying to figure out which marketing campaigns are successful without knowing where the traffic is coming from!
Another common example is in software development. When you're debugging a program (that's programmer speak for fixing errors), source strings can help you pinpoint the exact location of the problem in your code. Each line of code, or even specific functions, might have an associated source string that identifies the file and line number where it resides. This makes the debugging process far less painful, as you're not blindly searching through thousands of lines of code. Thank goodness for that, right?
And it doesn't stop there! In database management, source strings can be used to track the origin of data entries. This is particularly important for maintaining data integrity and ensuring that information is accurate and reliable. For example, if you're tracking sales data, you'd want to know where each sale originated from (e.g., online store, physical store, etc.) to get a clear picture of your business performance. Without this context, you're just looking at a bunch of numbers with no real meaning.
Consider also digital watermarking. Many images and videos online have a subtle, invisible source string embedded within them. This watermark can be used to prove ownership and track unauthorized distribution of the content. If you find your images are being used without permission, this little identifier can be your best friend. It's like having a digital fingerprint on your work, making it easier to protect your intellectual property. No more free-for-all with your hard-earned content!

Why Source Strings Matter
3. The Power of Context and Traceability
So, we've established that source strings are basically identifiers. But why all the fuss? Well, the true value lies in the context they provide. Data without context is like a puzzle piece with no picture to fit into. It's useless, and often, misleading. Source strings add that crucial context, allowing you to understand the "who, what, when, where, and why" behind the data. Without them, we're essentially flying blind.
Traceability is another key benefit. In many industries, especially those dealing with sensitive information like finance or healthcare, being able to trace the origin of data is not just helpful, it's legally required! Source strings provide an audit trail, allowing you to track data through various systems and processes. This is crucial for regulatory compliance, risk management, and simply ensuring that things are done properly. Nobody wants to be on the wrong side of the law, do they?
Imagine a hospital tracking patient data. They need to know exactly where each piece of information came from which doctor recorded it, which lab performed the test, etc. A reliable source string system allows them to quickly and accurately track this information, ensuring that patients receive the right treatment and that the hospital remains compliant with healthcare regulations. The stakes are high, and accuracy is paramount. Lives could literally depend on it!
Beyond compliance, traceability improves efficiency and accuracy. By knowing where data originated, you can quickly identify and correct errors, troubleshoot problems, and optimize processes. Its like having a GPS for your data, guiding you through the complexities of the digital landscape. No more wandering aimlessly hoping to find the right information. Source strings bring order to the chaos!
Potential Pitfalls
4. Source Strings
While source strings offer many benefits, it's essential to be aware of the potential downsides. Just like any powerful tool, they can be misused or exploited if not handled carefully. One major concern is security. If a source string is easily guessable or predictable, it could be used by malicious actors to spoof data or gain unauthorized access to systems. Imagine someone creating fake data with a seemingly legitimate source string to bypass security checks. Scary, right?
Another concern is privacy. Source strings can sometimes contain sensitive information about users, such as their location, browsing history, or personal preferences. If this information is not properly protected, it could be exposed to unauthorized parties, leading to privacy breaches and potential harm. For instance, if a website tracks your location using a source string embedded in a URL, that information could be intercepted and used to target you with unwanted advertising or even track your movements.
Therefore, it's crucial to implement appropriate security measures to protect source strings from unauthorized access and manipulation. This might involve encrypting sensitive data, using strong authentication protocols, and regularly auditing systems for vulnerabilities. Privacy should also be a top priority. Organizations should be transparent about how they use source strings and provide users with the ability to control their data. Remember, responsible data handling is not just good ethics; it's good business!
Furthermore, be mindful of the longevity of source strings. Information that seems harmless today might become sensitive in the future. A seemingly innocent source string tracking the version of a software application might later reveal vulnerabilities that could be exploited. Regularly review and update your source string practices to ensure that they remain secure and privacy-friendly in the face of evolving threats. It's an ongoing process, not a one-time fix.

Lexical Analysis. Ppt Download
Future Trends
5. What's Next for Source String Technology?
The world of technology is constantly evolving, and so are the applications of source strings. As data volumes continue to explode and become even more intertwined, the importance of accurate and reliable data lineage will only increase. We can expect to see source strings becoming even more sophisticated, capable of tracking data across complex, distributed systems. The Internet of Things (IoT), with its billions of interconnected devices, will undoubtedly rely heavily on advanced source string techniques to manage and secure the vast amounts of data generated.
Artificial intelligence (AI) and machine learning (ML) are also playing a role. AI-powered systems can analyze source strings to identify patterns, detect anomalies, and even predict future trends. For example, an AI algorithm could analyze source strings from customer feedback to identify emerging product issues or areas for improvement. This can lead to faster and more data-driven decision-making. Imagine being able to anticipate problems before they even occur!
Blockchain technology offers another interesting avenue for source string innovation. Blockchain's decentralized and immutable nature makes it ideal for creating tamper-proof audit trails. By embedding source strings within blockchain transactions, you can ensure that data provenance is verifiable and trustworthy. This could have significant implications for supply chain management, digital identity, and other applications where trust and transparency are critical. The possibilities are truly endless.
Ultimately, the future of source strings lies in their ability to provide greater context, traceability, and security in an increasingly complex and interconnected world. As technology advances, we can expect to see even more innovative applications of source strings emerging, helping us make sense of the ever-growing flood of digital information. So, keep an eye out for those seemingly random characters they might just hold the key to unlocking the future!

Frequently Asked Questions (FAQ) About Source Strings
6. Your Burning Questions Answered
We know this can be a bit of a technical topic, so let's address some common questions you might have. We've tried to keep the answers as clear and concise as possible, without getting too bogged down in jargon.
7. FAQ 1
Good question! While both provide information about data, they serve slightly different purposes. Metadata is a broader term that encompasses all types of data about data, such as file size, creation date, and author. A source string is a specific type of metadata that focuses on identifying the origin or lineage of the data. Think of metadata as the general information about a file, and the source string as the specific label that says, "This is where it came from!" Both are useful, but the source string is focused on traceability.
8. FAQ 2
Not necessarily. Source strings can be embedded in various ways, some visible (like in a URL) and some invisible (like in image metadata or code). It depends on the specific application and how the source string is implemented. Some are designed to be easily accessible, while others are intentionally hidden to protect sensitive information or prevent tampering. So, sometimes you see them, sometimes you don't! It's all part of the mystery.
9. FAQ 3
Unfortunately, yes. Just like any piece of information, source strings can be forged or altered by malicious actors. This is why it's crucial to implement security measures to protect source strings from tampering. Using techniques like digital signatures or blockchain can help ensure the integrity and authenticity of source strings. Always be skeptical and verify the source of information whenever possible!